Search results
Appearance
There is a page named "VIC cipher" on Wikipedia
- The VIC cipher was a pencil and paper cipher used by the Soviet spy Reino Häyhänen, codenamed "VICTOR". If the cipher were to be given a modern technical...19 KB (2,685 words) - 12:31, 28 July 2024
- The Vigenère cipher (French pronunciation: [viʒnɛːʁ]) is a method of encrypting alphabetic text where each letter of the plaintext is encoded with a different...44 KB (5,934 words) - 09:14, 24 August 2024
- In cryptography, a transposition cipher (also known as a permutation cipher) is a method of encryption which scrambles the positions of characters (transposition)...25 KB (3,604 words) - 03:23, 21 March 2024
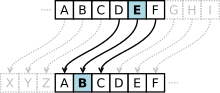
- In cryptography, a Caesar cipher, also known as Caesar's cipher, the shift cipher, Caesar's code, or Caesar shift, is one of the simplest and most widely...19 KB (2,031 words) - 00:56, 12 August 2024
- Look up VIC, Vic, vic, or Vic. in Wiktionary, the free dictionary. Vic, vic or VIC may refer to: Vic (name), a list of people, fictional characters and...3 KB (458 words) - 19:25, 17 June 2024
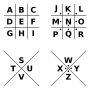
- pigpen cipher (alternatively referred to as the masonic cipher, Freemason's cipher, Rosicrucian cipher, Napoleon cipher, and tic-tac-toe cipher) is a geometric...10 KB (1,226 words) - 23:22, 25 June 2024
- Straddling checkerboard (redirect from Straddling cipher)checkerboard cipher". www.crittologia.eu. Retrieved 2024-01-30. David Kahn. "Number One From Moscow". 1993. "Straddling Cipher" The VIC Cipher Straddling...9 KB (1,029 words) - 22:05, 30 January 2024
- The Playfair cipher or Playfair square or Wheatstone–Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution...20 KB (2,503 words) - 16:11, 28 July 2024
- In the history of cryptography, the Nihilist cipher is a manually operated symmetric encryption cipher, originally used by Russian Nihilists in the 1880s...6 KB (805 words) - 03:28, 28 December 2023
- In cryptography, a substitution cipher is a method of encrypting in which units of plaintext are replaced with the ciphertext, in a defined manner, with...30 KB (4,021 words) - 22:15, 14 July 2024
- null cipher, also known as concealment cipher, is an ancient form of encryption where the plaintext is mixed with a large amount of non-cipher material...11 KB (1,496 words) - 22:12, 28 June 2024
- The rail fence cipher (also called a zigzag cipher) is a classical type of transposition cipher. It derives its name from the manner in which encryption...7 KB (1,103 words) - 16:01, 16 September 2023
- Atbash (redirect from Atbash cipher)(Hebrew: אתבש; also transliterated Atbaš) is a monoalphabetic substitution cipher originally used to encrypt the Hebrew alphabet. It can be modified for use...7 KB (645 words) - 11:15, 24 April 2024
- Enigma machine (redirect from Enigma cipher machine)The Enigma machine is a cipher device developed and used in the early- to mid-20th century to protect commercial, diplomatic, and military communication...93 KB (11,271 words) - 16:28, 8 August 2024
- The Two-square cipher, also called double Playfair, is a manual symmetric encryption technique. It was developed to ease the cumbersome nature of the large...11 KB (1,673 words) - 19:08, 29 June 2024
- In cryptography, a classical cipher is a type of cipher that was used historically but for the most part, has fallen into disuse. In contrast to modern...15 KB (2,528 words) - 02:24, 15 June 2024
- Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation...8 KB (773 words) - 15:51, 6 March 2024
- In classical cryptography, the running key cipher is a type of polyalphabetic substitution cipher in which a text, typically from a book, is used to provide...10 KB (1,294 words) - 19:13, 30 July 2024
- One-time pad (redirect from Vernam cipher)communicating parties. It has also been mathematically proven that any cipher with the property of perfect secrecy must use keys with effectively the...57 KB (7,618 words) - 17:20, 19 July 2024
- polyalphabetic cipher is a substitution, using multiple substitution alphabets. The Vigenère cipher is probably the best-known example of a polyalphabetic cipher, though...6 KB (683 words) - 07:58, 14 March 2024
- Number 4 The Lost Cipher by Stanley J. Weyman 2816465McClure's Magazine, Volume 5, Number 4 — The Lost CipherStanley J. Weyman THE LOST CIPHER. A STORY OF THE
- Gravity Falls (2012-2016) Oh, Gravity Falls, it is good to be back! Bill Cipher Be careful Jennifer, the unspeakable horrors nearby, it could be anywhere
- must be able to read anything at sight. Sometimes the music is marked in ciphers that look like anything from a whale to an anchor. Then you have to be