Search results
Appearance
There is a page named "Cryptographic Module Validation Program" on Wikipedia
- Cryptographic Module Validation Program (CMVP) is a joint American and Canadian security accreditation program for cryptographic modules. The program...2 KB (195 words) - 18:20, 29 April 2024
- FIPS 140-2 (category Cryptography standards)Cryptographic Modules Testing laboratories perform validation testing of cryptographic modules. Cryptographic modules are tested against requirements found in FIPS...16 KB (1,902 words) - 15:20, 10 January 2024
- "Cryptographic Module Validation Program". CSRC.nist.gov. Archived from the original on 2021-10-21. "Modules In Process List - Cryptographic Module Validation...42 KB (1,391 words) - 21:34, 18 June 2024
- implementing cryptographic modules. Standards for cryptographic modules include FIPS 140-3 and ISO/IEC 19790. Cryptographic Module Validation Program (CMVP)...2 KB (140 words) - 18:20, 29 April 2024
- FIPS 140-3 (category Cryptography standards)integrity testing. The FIPS 140 standard established the Cryptographic Module Validation Program (CMVP) as a joint effort by the NIST and the Communications...8 KB (905 words) - 11:42, 24 September 2023
- Voluntary Laboratory Accreditation Program (NVLAP) accredits CMTLs to meet Cryptographic Module Validation Program (CMVP) standards and procedures. This...3 KB (387 words) - 08:21, 1 March 2024
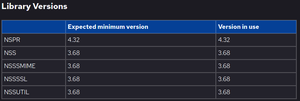
- Network Security Services (category Cryptographic software)Inc. "Cryptographic Module Validation Program: Certificate #1280". NIST. 2010-03-29. module: Network Security Services (NSS) Cryptographic Module, vendor:...13 KB (1,249 words) - 03:38, 1 July 2024
- FIPS 140 (category Cryptography standards)the validation is applicable is also listed. Vendors do not always maintain their baseline validations. The Cryptographic Module Validation Program (CMVP)...12 KB (1,479 words) - 23:12, 11 January 2024
- OpenSSL (category Cryptographic software)"Cryptographic Module Validation Program Certificate #1747". Computer Security Resource Center. October 11, 2016. "Cryptographic Module Validation Program...50 KB (4,338 words) - 16:31, 5 July 2024
- Secure Hash Algorithms (category Cryptography)functions, are subject to official validation by the CMVP (Cryptographic Module Validation Program), a joint program run by the American National Institute...3 KB (464 words) - 12:44, 20 May 2024
- Crypto++ (category Cryptographic software)(PDF). Cryptographic Module Validation Program (CMVP). 2007. Retrieved 2010-08-08. "Validated FIPS 140-1 and FIPS 140-2 Cryptographic Modules (2003)"...19 KB (1,314 words) - 19:15, 16 February 2024
- environments. LEA is one of the cryptographic algorithms approved by the Korean Cryptographic Module Validation Program (KCMVP) and is the national standard...19 KB (2,868 words) - 14:58, 26 January 2024
- ISO/IEC 19790 (category Cryptography)requirements for cryptographic modules". www.iso.org. Retrieved 2023-09-24. "Standards - Cryptographic Module Validation Program". csrc.nist.gov. Archived...3 KB (269 words) - 18:04, 30 December 2023
- for digital signatures, strong authentication and other cryptographic functions. These modules traditionally come in the form of a plug-in card or an external...13 KB (1,528 words) - 23:26, 27 June 2024
- Advanced Encryption Standard (category Cryptography)validation in no way implies that the cryptographic module implementing the algorithm is secure. A cryptographic module lacking FIPS 140-2 validation...49 KB (5,600 words) - 15:27, 5 July 2024
- Security level (redirect from Cryptographic strength)2017-01-02. "Implementation Guidance for FIPS 140-2 and the Cryptographic Module Validation Program" (PDF). "The rho method". Retrieved 21 February 2024. Barker...13 KB (1,360 words) - 04:38, 10 May 2024
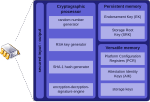
- The Trusted Platform Module (TPM) provides: A hardware random number generator Facilities for the secure generation of cryptographic keys for limited uses...79 KB (6,479 words) - 23:40, 8 June 2024
- decrypted in the issuer's security module and then validated on the basis of the techniques for on-line local PIN validation. There are different transaction...7 KB (1,030 words) - 20:35, 23 February 2024
- operational and running system. NetApp has passed NIST Cryptographic Module Validation Program for its NetApp CryptoMod (TPM) with ONTAP 9.2. MetroCluster...43 KB (4,380 words) - 02:30, 27 April 2024
- B Cryptography was a set of cryptographic algorithms promulgated by the National Security Agency as part of its Cryptographic Modernization Program. It...8 KB (901 words) - 16:26, 24 December 2022
- Computer Applications. c. FIPS PUB 140-1, Security Requirements for Cryptographic Modules. d. FIPS PUB 171, Key Management Using ANSI X9.17. e. FIPS PUB 180-1
- Info and Validation The Extra Info tab offers room for a summary of the results and a diagnosis. The Validation tab provides a cryptographic digest hash